More Innovation:
Artificial Intelligence in Cybersecurity: The Benefits and Challenges
Updated: November 18, 2021
Artificial Intelligence in Cybersecurity: For Good or Bad
After an explosion in the early 1860s killed his younger brother, Alfred Nobel invented dynamite, allowing miners and prospectors to dig through stone faster and safer.
However, Alfred Nobel was saddened and regretted his invention when he soon discovered that people used dynamite to harm others. Worried about his legacy, Alfred Nobel created the Nobel Prizes to reward those who have conferred the greatest benefit to humankind.
Similar to dynamite, artificial intelligence (AI) is only a tool, and it’s up to us to choose how we use it.
Throughout this article, we’ll highlight how AI is used to protect organizations. But we’ll also show you how AI is used to hack and steal from organizations.
Before we begin, let’s start by addressing the growth of artificial intelligence in cybersecurity today.
The Growth of Artificial Intelligence in Cybersecurity
AI is a well-known asset for businesses that use automation to increase productivity and streamline tasks. One crucial application that leverages AI more than any other today is data security, or cybersecurity (Source: IBM). With the economy going through a digital transformation and data breaches increasing by the day, AI might be our best chance at safeguarding our information.
The global market for artificial intelligence in cybersecurity is projected to reach $46.3 billion by 2027, at a compound annual growth rate (CAGR) of 23.6% during the forecast period (Source: Meticulous Research). This stems from the increasing complexity and frequency of cyber threats, leading to a need for disruptive cybersecurity solutions.
This explosive growth results from increasing government investment in the security sector and the requirement for cloud-based security solutions among businesses regardless of size or industry. As the network capacity grows with 5G technology and improved cloud services, so does the growth of artificial intelligence and the arms race between cyberattacks and cybersecurity.
Data Breaches: The Need for Better Cybersecurity
As technology progresses, more of our information has been moving to the digital world. As a result, cyberattacks are increasingly common and costly. Business organizations, for example, are desirable targets to cybercriminals simply due to the large amount of data that hackers can steal in a single attack.

Globally, a company’s average total cost per data breach was $3.86 million in 2020 (Source: Ponemon Institute). The Ponemon Institute study identified that organizations with fully deployed security automation saved on average $3.58 million compared to those with no security automation in place.
When used in conjunction with traditional methods, AI is a powerful tool for protecting against cyber attacks. In the digital age, shielding assets and operations from hackers is more challenging than ever. The numbers are staggering – Cisco alone reported that they blocked seven trillion threats on behalf of their customers in 2018 (Source: Capgemini Research Institute).
At the same time, the adoption of artificial intelligence is not without risks: more than 60% of companies adopting AI recognize cybersecurity risks generated by AI-powered threats as the most relevant ones to business operations (Source: McKinsey and Company). Although AI provides organizations with the tools to fend off malicious attacks in the wrong hands, it can supply cybercriminals with avenues to take advantage of systems.
The following sections will go over the main functions of AI in cybersecurity and the benefits and drawbacks the technology offers to protect data.
Artificial Intelligence in Cybersecurity: The 3 Main Functions
In the domain of cybersecurity, AI has three primary functions:
- Detection
- Prediction
- and Response
Detection
Today, organizations use AI extensively to detect cyber threats. Over 50% of organizations implementing AI-based cybersecurity solutions have a high usage rate for detection purposes (Source: Capgemini Research Institute). Detection reflects the unique capabilities of AI, through machine learning or deep learning, to use behavioural analysis to identify irregular traffic continuously.
For example, Honeywell recently launched their Secure Media Exchange (SMX) solution, which leverages AI to detect threats introduced via USB devices to disrupt operations by misusing legitimate USB functions or unauthorized device actions. (Source: HelpNet Security).
Prediction
The prediction function holds the second-highest usage rate. Roughly 35% of organizations make extensive use of AI to predict cyber threats. By scanning through vast data types, the AI makes predictions based on the system’s training.
Organizations that employ AI for prediction purposes can use the technology to automatically identify their assets and network topology, identify critical vulnerabilities, and continuously improve their networks defences against any potential cyberattacks with destructive potential (Source: Progress).
Response
Lastly, when it comes to responding to threats, AI is still evolving. Only 18% of organizations make extensive use of AI to respond to cyber-attacks. This means automating the creation of a virtual patch for a detected threat or developing new protection mechanisms in real-time.
An AI response solution is straightforward, detecting attacks and stopping them while they are happening. U.S. specialty retailer Avenue deployed a machine learning-based solution to differentiate between normal and abnormal behaviour to combat bot attacks, shutting down bot-triggered anomalous behaviour like stolen credentials or unauthorized purchases on customer accounts (Source: Tech Crunch).
Regardless of how an organization uses its AI resources for cybersecurity, it helps them improve threat response time, lowers costs, and responds to breaches.
The Main Benefits of Artificial Intelligence in Cybersecurity
Among the main benefits that AI brings to cybersecurity, we can point out the following:
Threat Hunting
Successful threat hunting requires a pre-emptive search of large data sets, using AI and machine learning to power automated scanning. This approach to AI is proactive rather than reactive. The idea is to identify threats continuously that may or may not have already evaded the current detection capabilities (Source: IEEE Computer Society).
However, it’s crucial to incorporate the AI approach with traditional security techniques, also known as signature-based systems. These include firewalls and malware detection programs. Signature-based methods are efficient in battling previously encountered threats. Still, AI methods are more effective to identify threats that have not been discovered yet, going through large volumes of data, and integrating behavioural analysis.
Automating threat hunting with AI enables faster response times and improved recommendations on responses. It provides the information needed to reduce attack vectors, breaches and allows organizations to move from a purely reactive response to operating ahead of threats, predicting new attacks based on past occurrences and data.
Vulnerability Management
Unlike threat hunting, which focuses on identifying and neutralizing incoming malicious agents to the system, vulnerability management identifies weak spots within the organization’s network environment and assets.
With AI tools, organizations can analyze the baseline behaviour of user accounts, endpoints, and servers, identifying abnormal behaviour that might signal an unknown attack. This helps organizations protect themselves from potential threats targeting system weaknesses. Vulnerability management includes identifying vulnerabilities in IT assets, evaluating risk, and taking appropriate action across systems or networks (Source: Tool Box).
Thanks to machine learning and deep learning techniques, cybersecurity systems can learn and evolve from each success and failure it experiences, optimizing performance for future encounters in real-time to assure the network’s integrity.
Network Security
Many attacks succeed because organizations don’t set well-timed policies or apply firmware updates or patches to all devices throughout the network. As new technologies constantly flood the market, providing a competitive advantage, organizations are pressured to incorporate them into their network, compromising security quickly.
Organizations can leverage AI to improve network security by learning network traffic patterns and recommending functional groupings of workloads and security policies based on specific needs. Additionally, AI can help manage the vast number of connected devices navigating their firmware updates and security patches automatically – something that would take considerably more time and potentially increase risk if done manually.
Additionally, AI for network security can be combined with other innovative technologies such as blockchain. Blockchain enables secure storage, data sharing and helps security management identify criminal identity loopholes in the system. Combining AI and blockchain, organizations can guarantee a higher security standard for their data and avoid compromising the whole system against an attack (Source: World Economic Forum).
Interested in hearing more about how blockchain technology is being used in cybersecurity? Find out in our latest article “The Benefits and Vulnerabilities of Blockchain Security.”
The Challenges of Artificial Intelligence in Cybersecurity
Despite the many benefits AI brings to cybersecurity systems, it doesn’t come without challenges and limitations. The drawbacks of implementing artificial intelligence into cybersecurity present themselves in two primary forms: usage by cybercriminals and the high adoption barriers.
Cybercriminals Also Use AI
AI is a dual-use technology, being used both for offence and defence. On the offensive, AI supports malicious attacks and can make them even more effective, increasing their precision and identifying more attack points on a network.
Although we learned AI is a powerful tool for defensive purposes, it has a major disadvantage. Cybersecurity is restricted by regulations that hackers are not. High-risk applications, understood as systems that use AI for critical infrastructure, safety, and deal with confidential information, are usually strictly Government-regulated (Source: CEPS). Unfortunately, this may limit how an organization can use artificial intelligence defensively.

On the other hand, as the cost of developing applications diminishes and the attack surface increases for cyber threats, it becomes easier for criminals to leverage the technology for harmful purposes.
AI technology allows for faster, more precise, and destructive hacking, introducing a new wave of malicious attacks.
Hackers commonly use one popular program analysis technique, known as fuzzing, to find vulnerabilities in complex software (Source: Microsoft). This technique presents a target program with malicious input designed to cause buffer overflows, crashes, memory errors, and exceptions and expose system weaknesses.
Combined with AI, it becomes a severe cyber threat as hackers increase the precision and efficiency of their attacks, obtaining critical information on a system’s weaknesses more easily by combing through large data sets quickly.
Another example comes in the form of more effective phishing attacks. AI-powered phishing can quickly navigate sensitive data, and extract only the necessary information, to reduce traffic and make the malware harder to detect.
High Adoption Barriers
Companies need to invest considerable time and money in computing power, memory, and data centres to build and maintain artificial intelligence systems. Over time these costs have decreased with the advancement of technology, making quality servers more affordable.
Security automation effectiveness also continues to grow, becoming a prerequisite for any organization running on the cloud. Globally, businesses with no deployed security automation saw an average total data breach cost of $6 million. In comparison, those with fully deployed security automation had an average total cost of a data breach at $2.45 million. (Source: Ponemon Institute).
Cybersecurity automation powered by AI is becoming indispensable for organizations. The most significant roadblocks for its adoption and deployment are talent acquisition, data complexity, and the employment of proper AI tools (Source: IBM).
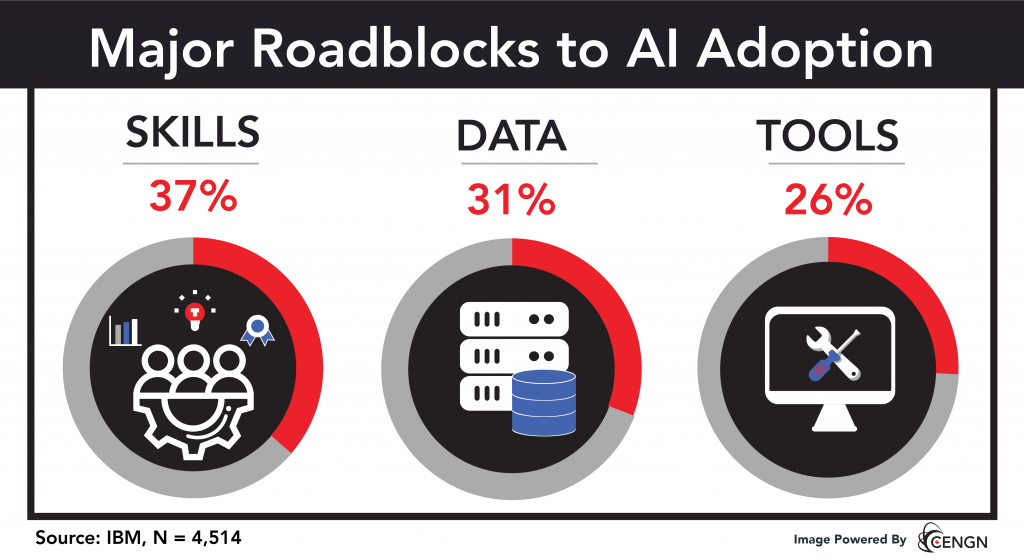
The skills gap is an important barrier for AI deployment in businesses today, with 37% of organizations expressing difficulty finding talent with the appropriate level of AI expertise and knowledge (Source: IBM). The need for AI skills is critical mainly to companies still exploring AI adoption. Those focused on AI deployment see data complexity and having the right toolset as crucial issues.
Check out CENGN Academy’s Machine Learning with Python course to overcome the skills barrier to AI coding.
Data complexity stems from keeping up with the large flow of data through the network and sourcing the correct data set of malicious codes and malware to use in AI model training. Organizations need to properly manage the enormous amount of different data types and data silos. Not only does this require skilled workers, but also the right toolset.
Tools refer to cyber solutions an organization integrates into its network. Many factors are essential to consider when choosing the right toolset, like whether an organization is locked in with a vendor or uses AI solutions from their cloud provider. The important thing is to get it right the first time, as it’s costly and challenging to switch tools.
Preparing For The Age of Artificial Intelligence Based Security
Network activity continues to grow, and just about all critical information is stored on the cloud. This reality means cyber threats are becoming more frequent, and organizations must prepare for faster and more compromising attacks on their system’s integrity. Artificial Intelligence is the answer, with adoption rates swiftly rising over the years and a proven track record of improving security and providing cost savings in the long run.
Nevertheless, it is essential to consider that cybercriminals also use AI to penetrate systems. So, organizations must not fall behind in this arms race and consider employing AI in their cybersecurity efforts to protect their network from malicious threats.
Are you interested in hearing more about artificial intelligence, cybersecurity, and other next-generation technologies?
Download our “Next Generation Network Imperative” Whitepaper to find out more.
The International Data Corporation (IDC), a world-renowned global market intelligence firm, was commissioned to complete this study.










